Technology Tips by Centrend Podcast: Episode 2
“Phishing” is a social hacking attempt to get you to reveal information that hackers can use to exploit your email or computer account. Here are some clues on how to detect a phishing attempt and what you should be looking for.
Welcome to Email Phishing Anatomy 101!
You cannot assume that an email you receive actually came from the sender it claims to be from. Phishers are very crafty and will do everything they can to appear familiar so that you will follow their call to action.
The infographic below illustrates a very clever phishing email.
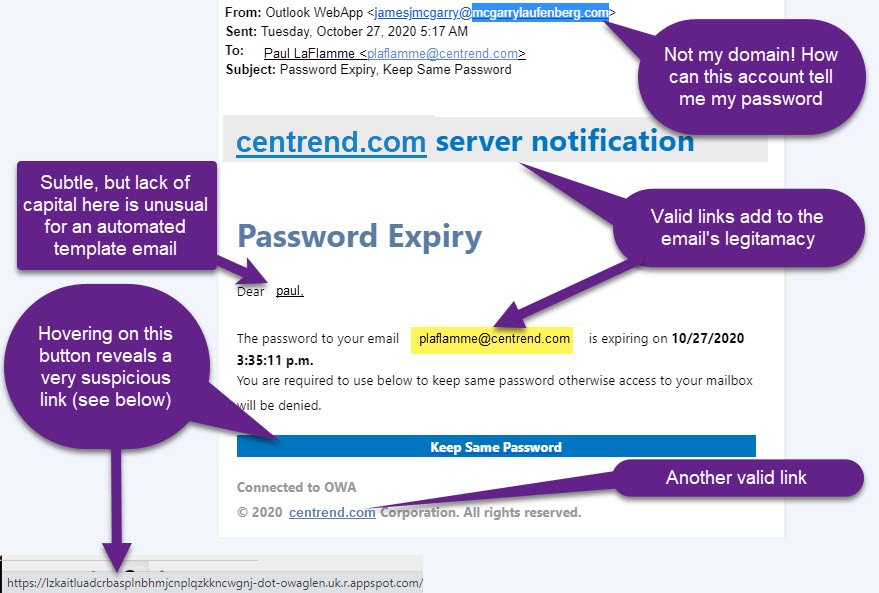
“Keep Same Password” Now, what would happen if the recipient actually clicks the button? Now, what would happen if you clicked the button? You would be taken to a website that looks like an Outlook Web Access Portal and asked to do the following things:
- They tell you to confirm your current login name and password to “renew” it.
- Upon submitting your name and password, you are taken to a screen that asks for previously used passwords for verification purposes.
- This process is open-ended. The more time you spend time submitting passwords, the more data they collect to hack into other systems at your organization.
 You can do several things in your business to reduce the amount of these types of emails that actually make it through.
You can do several things in your business to reduce the amount of these types of emails that actually make it through.
- Use a strong commercial-grade firewall with deep packet inspection.
- If you’re suspicious, don’t click the link. Instead, log in by going directly to the website yourself.
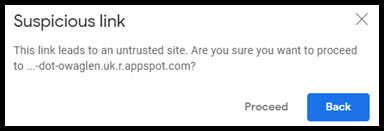
- Have strong endpoint security software on your workstations, so if you do click a link, you will get a warning like Centrend’s managed service clients get (see grap[hic at right)
Centrend works hard to protect our customers from phishing by blocking many of these types of threats from ever entering your network or email folder, to begin with. Everyone gets fooled, especially if you are in a hurry. For times like this, we make sure there is local workstation security to safely check suspicious links. For example, clicking on the email below in one of our managed services environments will give the email recipient a second chance to reconsider by showing the following message:
If you want to keep the phisherman from trolling your computer’s waters, give us a call or drop us a line.
